Last time I walked through the process of merging two sets of Kubernetest client configurations into one. For more ephemeral data, you might not want to munge it all into your main configuration. The KUBECONFIG environment variables lets you specify muiltiple configuration files and merge them into a single set of configuration data.
Merging two Kubernetes client configurations
I have two distinct Kubernetes clusters I work with on a daily basis. One is a local vagrant bases set of VM built by the Kubevirt code base. The other is a “baremetal” install of OpenShift Origin on a pair of Fedora workstation in my office. I want to be able to switch back and forth between them.
Continue reading
Getting started with helm on OpenShift
After attending in on a helm based lab at the OpenStack summit, I decided I wanted to try it out for myself on my OpenShift cluster.
Continue reading
Exploring OpenShift RBAC
OK, since I did it wrong last time, I’m going to try creating an user in OpenShift, and grant that user permissions to do various things.Â
Continue reading
Fixing Bug 96869
Bug 968696
The word Admin is used all over the place. To administer was originally something servants did to their masters. In one of the greater inversions of linguistic history, we now use Admin as a way to indicate authority. In OpenStack, the admin role is used for almost all operations that are reserved for someone with a higher level of authority. These actions are not expected to be performed by people with the plebean Member role.
OpenShift Origin Default Auth
Once I got the Ansible playbook to run, I was able to poke at the openshift setup.
The install creates a default configuration in the Ansible users home directory on the master node.
Installing OpenShift Origin via Ansible on Fedora 25
While many people referred me to run one of the virtualized setups of OpenShift, I wanted something on baremetal in order to eventually test out KubeVirt. Just running
oc cluster up
As some people suggested did not work, as it assumes prerequisites are properly set up; the docker registry was one that I tripped over. So, I decided to give openshift-ansible a test run. Here are my notes.
Why Quotas are Hard
A quota is a numerical limit on a group of resources. Quotas have to be both recorded and enforced.
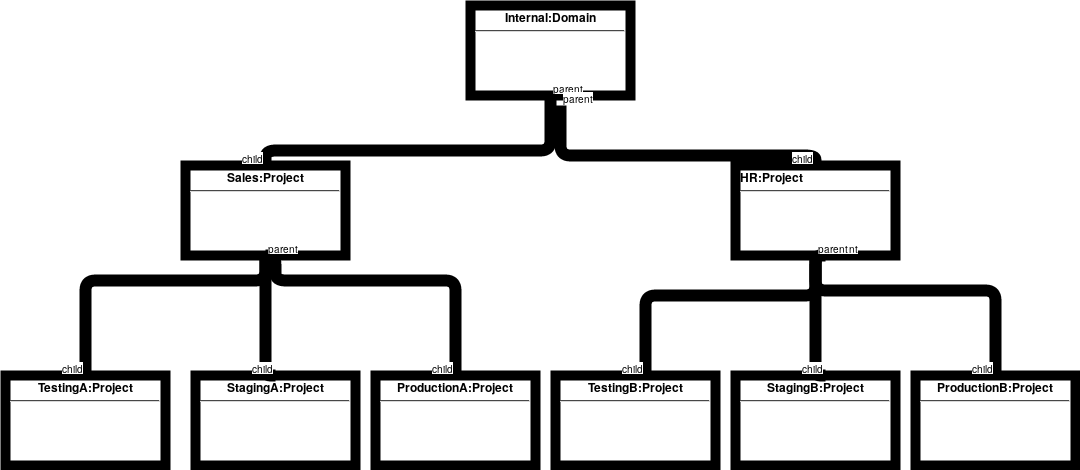
We had a session at the summit this past week about hierarchical quotas and, if I took anything away from it, it is that quotas are hard.
Keystone supports a project hierarchy. Here’s a sample one for you:
Using the OPTIONS Verb for RBAC
Lets say you have a RESTful Web Service. For any given URL, you might support one or more of the HTTP verbs: GET, PUT, POST, DELETE and so on. A user might wonder what they mean, and which you actually support. One way of reporting that is by using the OPTION Verb. While this is a relatively unusual verb, using it to describe a resource is a fairly well known mechanism. I want to take it one step further.
Continue readingInstalling R Packages in Fedora as a user
When I was trying to run R code that required additional packages, I got the error message:
Installing packages into ‘/usr/lib64/R/library’ (as ‘lib’ is unspecified) Warning in install.packages(new.pkg, dependencies = TRUE) : 'lib = "/usr/lib64/R/library"' is not writable
