This is more musing than a practical design.
Most application servers have a means to query LDAP for the authorization information for a user. This is separate from, and follows after, authentication which may be using one of multiple mechanism, possibly not even querying LDAP (although that would be strange).
And there are other mechanisms (SAML2, SSSD+mod_lookup_identity) that can, also, provide the authorization attributes.
Separating mechanism from meaning, however, we are left with the fact that applications need a way to query attributes to make authorization decisions. In Keystone, the general pattern is this:
A project is a group of resources.
A user is assigned a role on a project.
A user requests a token for a project. That token references the users roles.
The user passes the token to the server when accessing and API. Access control is based on the roles that the user has in the associated token.
The key point here is that it is the roles associated with the token in question that matter. From that point on, we have the ability to inject layers of indirection.
Here is where things fall down today. If we take an app like WordPress, and tried to make it query against Red Hat’s LDAP server for the groups to use, there is no mapping between the groups assigned and the permissions that the user should have. As the WordPress instance might be run by any one of several organizations within Red Hat, there is no direct mapping possible.
If we map this problem domain to IPA, we see where things fall down.
WordPress, here, is a service. If the host it is running on is owned by a particular organization (say, EMEA-Sales) it should be the EMEA Sales group that determines who gets what permissions on WordPress.
Aside: WordPress, by the way, makes a great example to use, as it has very clear, well defined roles, which have a clear scope of authorization for operations.
Subscriber < Contributor < Author < Editor < Administrator
Back to our regular article:
If we define and actor as either a user or agroup of users, a Role assignment is a : (actor, organization, application, role)
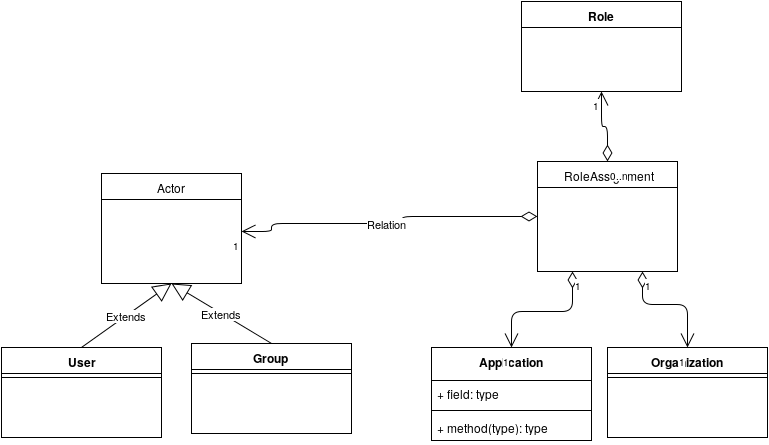
Now, a user should not have to go to IPA, get a token, and hand that to WordPress. When a user connects to WordPress, and attempts to do any non-public action, they are prompted for credentials, and are authenticated. At this point, WordPress can do the LDAP query. And here is the question:
“what should an application query for in LDAP”
If we use groups, then we have a nasty naming scheme. EMEA-sales_wordpress_admin versus LATAM-sales_worpress_admin. This is appending the query (organization, application) and the result (role).
Ideally, we would tag the role on the service. The service already reflects organization and application.
In the RFC based schemas, there is a organizationalRole objectclass which almost mirrors what we want. But I think the most important thing is to return an object that looks like a Group, most specifically groupofnames. Fortunately, I think this is just the ‘cn’.
Can we put a group of names under a service? Its not a container.
‘ipaService’ DESC ‘IPA service objectclass’ AUXILIARY MAY ( memberOf $ managedBy $ ipaKrbAuthzData) X-ORIGIN ‘IPA v2’ )
objectClass: ipaobject
objectClass: top
objectClass: ipaservice
objectClass: pkiuser
objectClass: ipakrbprincipal
objectClass: krbprincipal
objectClass: krbprincipalaux
objectClass: krbTicketPolicyAux
It probably would make more sense to have a separate subtree service-roles, with each service-name a container, and each role a group-of-names under that container. The application would filter on (service-name) to get the set of roles. For a specific user, the service would add an additional filter for memberof.
Now, that is a lot of embedded knowledge in the application, and does not provide any way to do additional business logic in the IPA server or to hide that complexity from the end user. Ideally, we would have something like automember to populate these role assignments, or, even better, a light-weight way for a user with a role assignment to re-delegate that to another user or principal.
That is what really gets valuable: user self service for delegation. We want to make it such that you do not need to be an admin to create a role assignment, but rather (with exceptions) you can delegate to others any role that you have assigned to yourself. This is a question of scale.
However, more than just scale, we want to be able to track responsibility; who assigned a user the role that they have, and how did they have the authority to assign it? When a user no longer has authority, should the people they have delegated to also lose it, or does that delegation get transferred? Both patterns are required for some uses.
I think this fast gets beyond what can be represented easily in an LDAP schema. Probably the right step is to use something like automember to place users into role assignments. Expanding nested groups, while nice, might be too complicated.
